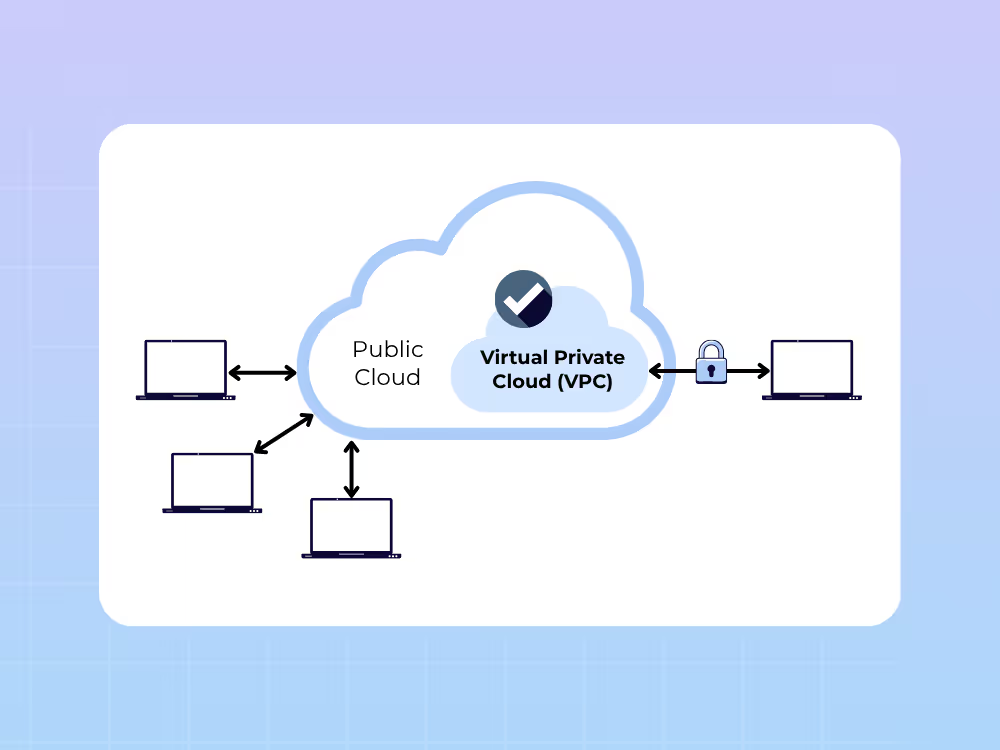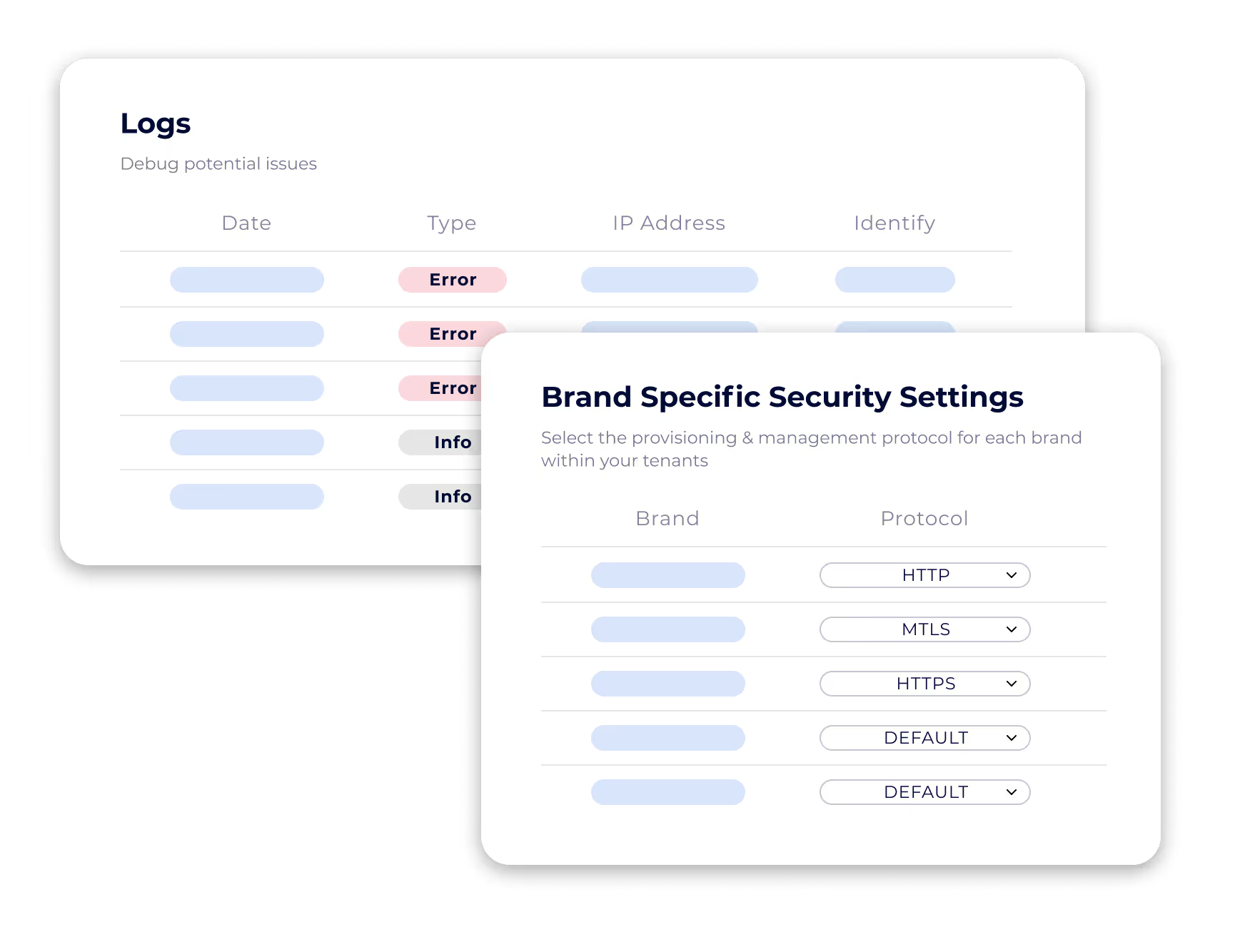

Enforce security and configuration standards automatically.

Apply predefined settings for device consistency at scale.

Set and manage firmware versions for all devices in one place.

Prevents rogue traffic and known exploit attempts at the device level.